Advanced Custom Fields (ACF) recently patched a missing authorization vulnerability in version 5.12.1 that potentially affects more than a million users. The security issue was discovered by Keitaro Yamazaki of Ierae Security, Inc, who reported it to the Information-technology Promotion Agency (IPA).
According to the CVE record information, the vulnerability affects all free versions of ACF prior to 5.12.1 and ACF Pro versions prior to 5.12.1. It allows a remote authenticated attacker to view the information on the database without the correct access permission. The National Vulnerability Database gives this particular vulnerability a 6.5 Medium score.
ACF product manager Iain Poulson explained that there are certain conditions necessary to make an attack possible.
“In particular, the attacker would have to already possess an account on the site at contributor-level or higher, so they’d likely be someone known to the site’s owners,” Poulson said. “There are a number of other conditions that would all have to be present for the attack to be successful. I’d rather not go into detail about exactly what those conditions are, as providing that information just increases the chances that someone will go looking for one of the few sites that matches those specifications.”
ACF released the patched version (5.12.1) on March 23, 2022, but the majority of the plugin’s two million users (~70%) are still running on older versions, leaving potentially more than a million users vulnerable.
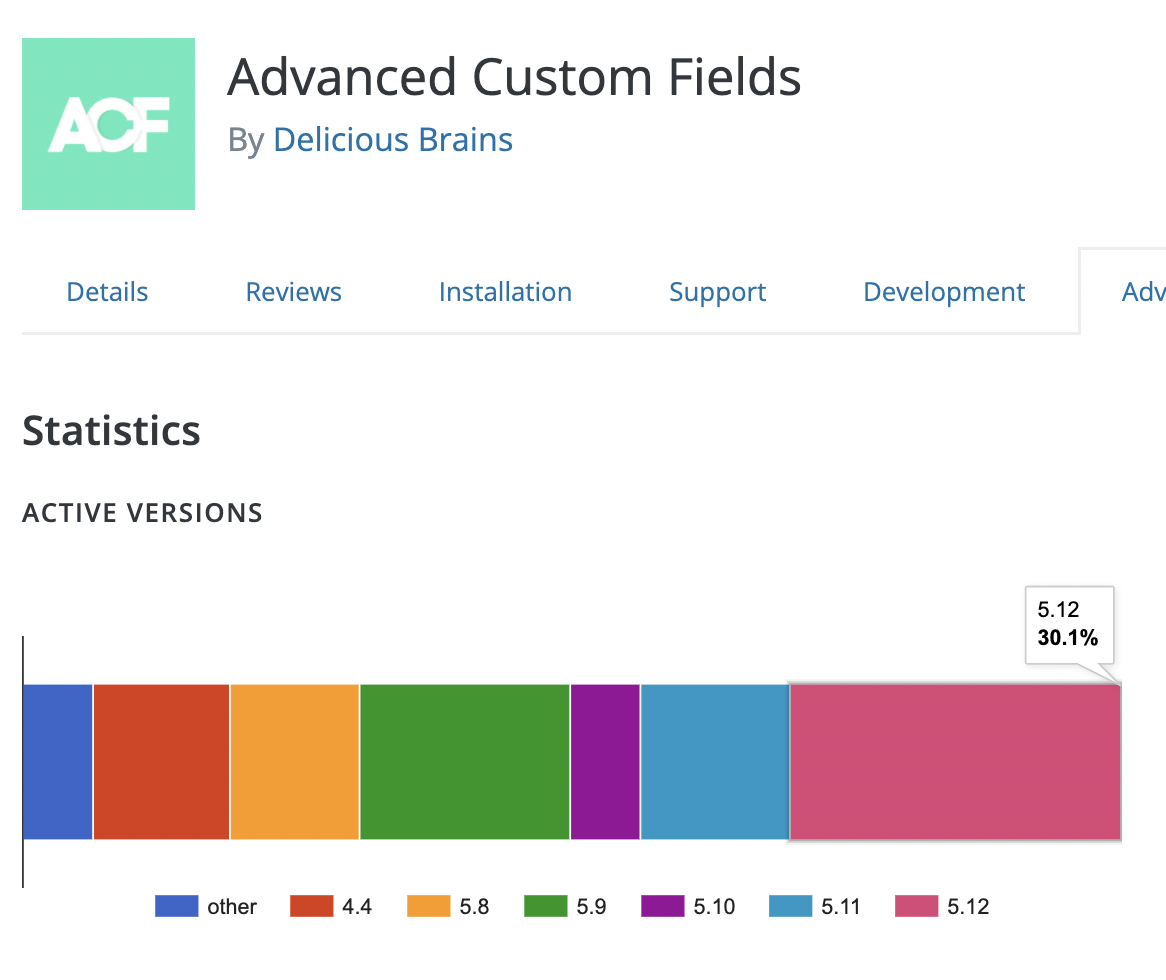 ACF Active Versions on 4/8/2022
ACF Active Versions on 4/8/2022
ACF’s changelog notes the fix in version 5.12.1 but doesn’t explicitly identify it as being a security fix. The plugin’s blog and Twitter accounts did not announce the update, so users may not know that their sites are vulnerable.
ACF representatives did not responded to our request for comment about why it was not specified as a security fix in the changelog. For sites that may have automatic updates turned off, the Japan Computer Emergency Response Team Coordination Center (JPCERT/CC) and the ACF team recommend users update to the latest version to protect their sites.





