Essential Addons for Elementor, a popular plugin with more than a million active installs, has patched a critical vulnerability that would allow for a local file inclusion attack.
The vulnerability was discovered by security researcher Wai Yan Myo Thet and reported to Patchstack on January 25, 2022. Patchstack customers received a virtual patch the same day. The issue was already known to the plugin’s developers, WPDeveloper, who issued two insufficient patches before it was ultimately fixed in version 5.0.5.
Patchstack published a summary of the vulnerability and explained how WordPress sites using the plugin could be compromised:
This vulnerability allows any user, regardless of their authentication or authorization status, to perform a local file inclusion attack. This attack can be used to include local files on the filesystem of the website, such as /etc/passwd. This can also be used to perform RCE by including a file with malicious PHP code that normally cannot be executed.
It’s important to note that the vulnerability primarily impacts users who have the dynamic gallery and product gallery widgets in use.
The plugin’s changelog makes the update seem more like an enhancement than a serious security concern, so users may not be fully aware that they need to update:
5.0.5 – 28/01/2022
Improved: Enhanced Security to prevent inclusion of unwanted file form remote server through ajax request
5.0.4 – 27/01/2022
Improved: Sanitized template file paths for Security Enhancement
Added: Support for new Capability Queries for WordPress 5.9
Fixed: Elementor Popups not being triggered
Few minor bug fixes & improvements
All versions earlier than 5.0.5 are considered vulnerable. WordPress.org stats don’t break down active installs according to minor versions, but approximately 54% of the plugin’s users are running versions older than 5.0.
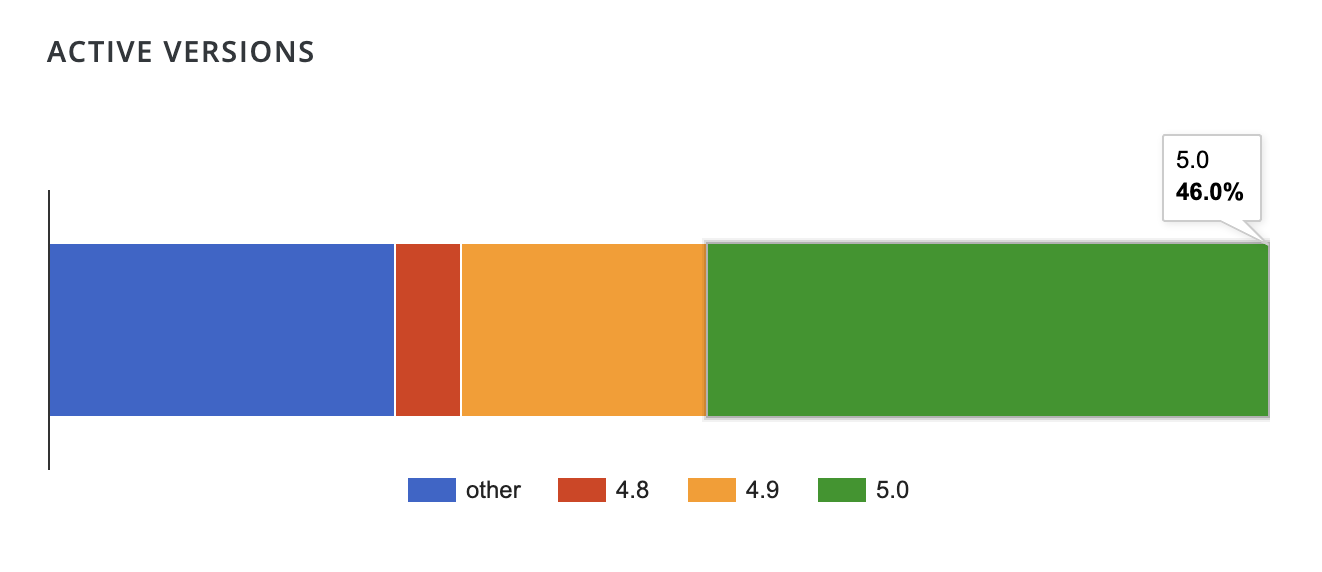
While this might seem like more than half a million users are still vulnerable, they would also need to be using the specific widgets in question. If you are not sure if you are using these widgets in combination, it’s best to simply update as soon as possible anyway.
Source





